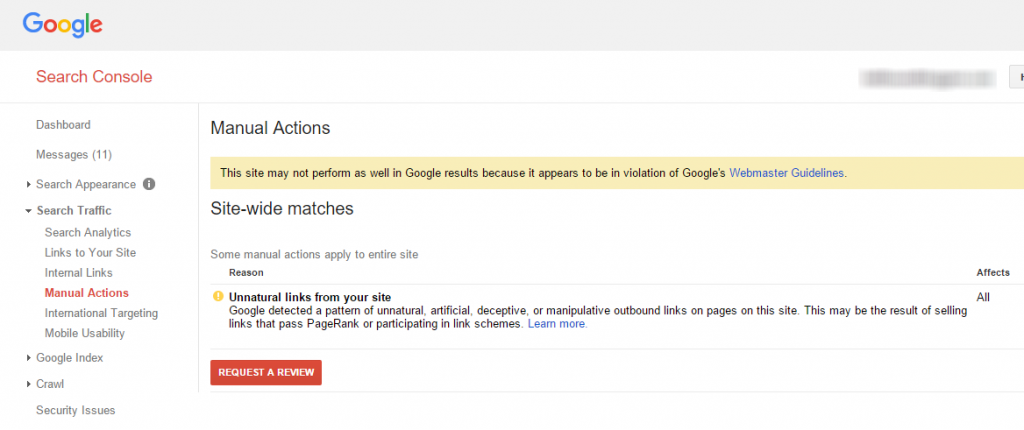
Google Hacked Site Review
The Google Hacking Database (GHDB) is an authoritative source for querying the ever-widening scope of the Google search engine. In the GHDB, search terms for files containing usernames, vulnerable servers, and even files containing passwords can be found here.

Hackers controlled the Google Morocco domain
Hack caused major outages for some clients including local councils and ‘potentially accessed public sector data ‘ Outsourcing group Capita, which runs crucial services for the NHS and.

Google Hacking Basic
The Exploit Database is a repository for exploits and proof-of-concepts rather than advisories, making it a valuable resource for those who need actionable data right away. The Google Hacking Database (GHDB) is a categorized index of Internet search engine queries designed to uncover interesting, and usually sensitive, information made publicly.
Google Hacking Database Net Effects
Pastes you were found in. A paste is information that has been published to a publicly facing website designed to share content and is often an early indicator of a data breach. Pastes are automatically imported and often removed shortly after having been posted. Using the 1Password password manager helps you ensure all your passwords are strong and unique such that a breach of one service.
GOOGLE HACKED BY LIZARDSQUAD Lizard Squad Hack Hijack Google
Here are my favorites. BreachAlarm. You can use BreachAlarm in the same way you use HaveIBeenPwned. It’s easy to search the site’s database to find past hacks and leaks that might include your.

The Google Hacking Database A Key Resource to Exposing Vulnerabiliti
Google Cloud databases provide you the best options in industry-leading reliability, global scale, and open standards for building data-driven applications. Get started for free Contact sales.

Google Provides Tips And Case Studies On How To Fix Hacked Sites
As a first step, follow the steps outlined in our article on securing a hacked or compromised Google account . After regaining access, enabling 2-step verification on your account is.

Google Hacking Database GHDB THE CURRENT HACKING NEWS CYBER
The Exploit Database is a repository for exploits and proof-of-concepts rather than advisories, making it a valuable resource for those who need actionable data right away. The Google Hacking Database (GHDB) is a categorized index of Internet search engine queries designed to uncover interesting, and usually sensitive, information made publicly.

Google Hacking DragonJAR Seguridad Inform tica
An introduction to the Google Hacking Database (GHDB)https://www.exploit-db.com/google-hacking-database/Subscribe! http://goo.gl/0HBjNXFacebook: http://goo.g.

Google Hacked Numerous Google Accounts Stolen Tech koreaportal
T-Mobile has reported its second data breach this year, reporting that personal information belonging to hundreds of account holders was exposed in an attack between late February and March 2023.
Tutorial Google Hack Document Edition Learn and Share Learn and Share
Google Hacking is a method used by attackers to find sensitive information with respect to vulnerabilities in applications indexed by Google.. Probably the most renowned source is Johnny’s I Hack Stuff Google Hacking Database which contains a comprehensive list of terms used to search the Web for files containing authentication.

Google Launch Help for Hacked Sites State of Digital
By Craig S. Smith. March 2, 2020 at 7:00 a.m. EST. (iStock) When Wyze Labs announced late last year that data on 2.4 million users of its smart home security camera had been stolen, the hack was.

Google Plus Account Hack Hack Any Social Network
This is a list of data breaches, using data compiled from various sources, including press reports, government news releases, and mainstream news articles. The list includes those involving the theft or compromise of 30,000 or more records, although many smaller breaches occur continually.

What is Google Hacking Code Hotfix
For instance, a search for password audit tool oracle db if you’re hacking an Oracle database. If you have an account on the server that hosts the database, you can run a hash cracker like John the Ripper against the database’s password file. The location of the hash file is different depending on the database.

Google Hack
The Google Hacking Database contains user-submitted queries divided into different categories – such as vulnerable files, files containing passwords, information about the server and the software on it, finding online devices and so on.
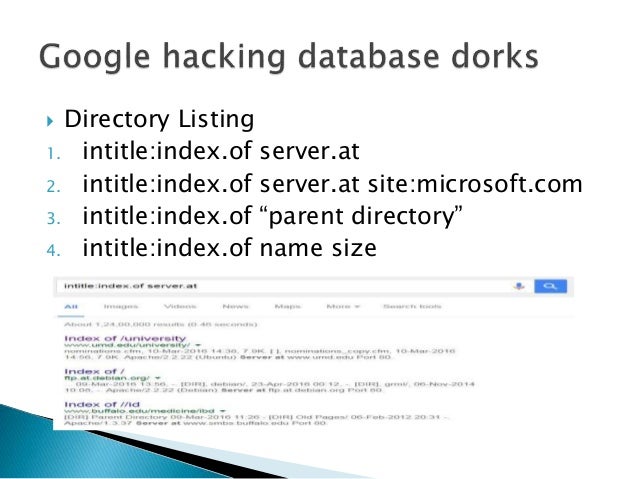
Introduction to google hacking database
Day One: 24 Hours to Gain Intel and Strategize. The task of Aggie Hack was to provide marketing insights for Z by HP using data analytics and machine learning. Our goal was to provide Z by HP with valuable customer segments and predict retention based on data analysis, clustering, classification modeling and customer lifetime value (CLV).